Ip Door Access Control
Our Products
CD/DVD Loader & Tower
CD/DVD Server + NAS
CD/DVD Loader & Server
CD/DVD Server
CD/DVD Duplicators
iSCSI (SAN) Storage
Pure NAS
Forensic Attached Tower(DAT)
Media Server
Custom Server
Services
Network Attached IP Door Access Control Systems from PrimeArray Systems
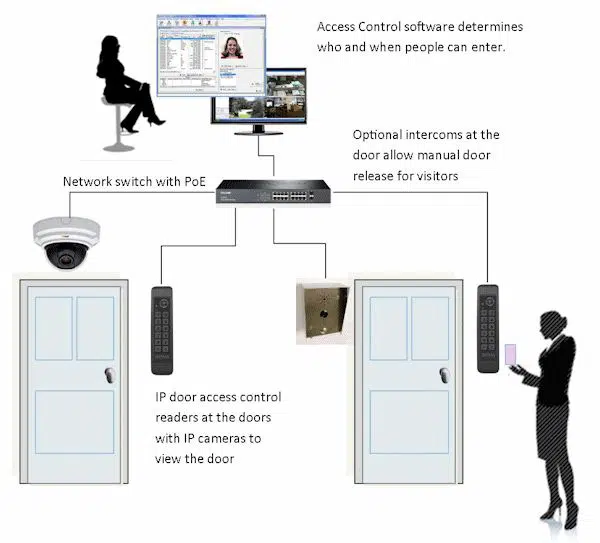
IP Based Door Access and Entry Control Systems Integrate with IP Camera Surveillance Systems to Provide a Complete Security System
Every ISONAS IP reader can be attached directly to the network. IP reader is powered using PoE. This type of modular IP based door control system enables you to add one door at a time and this helps you to save money because no expensive control system is now required. ISONAS IP door access contains all the functions in one unit. Previously, these functions had to be distributed among the reader and the control panel. Now even in those cases, when the network is down, each unit is capable of functioning as it is required to be.
A complete security system can now be developed by integrating IP based door access system with IP camera surveillance system. Convergence database software can be used to display door entry information along with the captured video. Similarly, intercoms can be integrated into the VMS platform and it helps you to gain manual control over entry of visitors and deliveries. Following given are some salient feature of IP based door access and entry control systems.
Features
- Includes free Crystal Matrix Software for all access system control
- No Control Panels Required
- IP Door Readers are powered using PoE
- The readers provide 12 VDC power for the electric lock
- Wide selection of credentials and cards
- Integrates with IP Camera security systems
- Works with IP intercoms to allow remote control of doors to allow entry of visitors
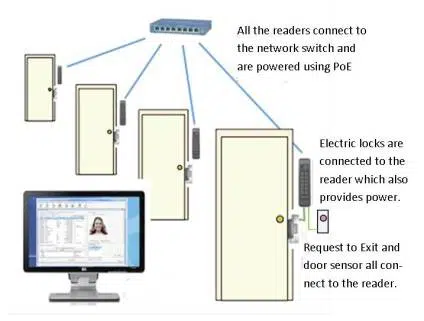
IP Door Readers
ISONAS IP door readers act both as a reader and a controller. Separate control panels are not required as the system is intelligently built and all controls lie within the unit.
It is possible to directly connect the IP reader to Ethernet network. The system is powered using PoE. The huge advantage of IP readers is that they are quite easy to install.
The ability of IP reader to convert the PoE power to 12 VDC allows the use of power lock without the inclusion of additional power wires. This can be done by using the CAT 5 drop to the reader. All you have to do is to select the PRX version that has the capability to read both ISONAS and HID format credentials, or the MCT version which includes the property of reading new Smart Card (ISO 14443) standard credentials.
There is a built-in intelligence system in IP readers and this helps to keep them working in the cases when the network is down. However, it is best to use Uninterruptible Power Supply (UPS) for the network switch that is providing the PoE.

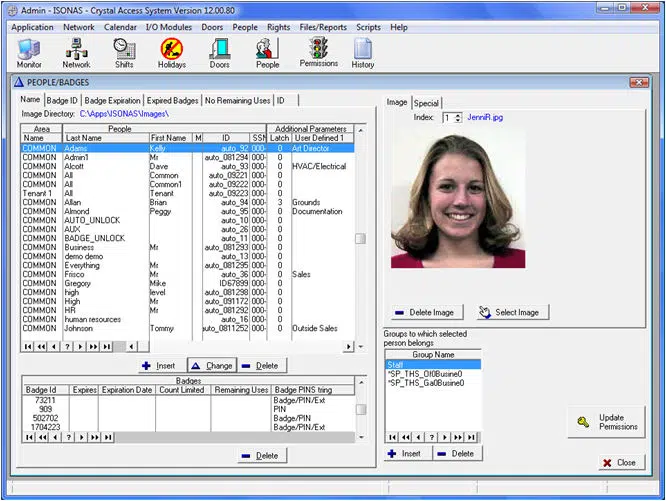
Access Control Software
DB Crystal Matrix Software™ is a free framework and is executed on windows PC. It provides an easy enrollment, thus providing you with the ease of selection of who, where and when are people allowed to come in. DB Crystal Matrix uses SQL data structure and makes it quite easy to integrate the system with video recording systems.
In order for you to optimize your access control system you can use EasyWeb 2015. For the easy registration user rights, it is recommended to add Active Directory Bridge. DB Crystal Matrix Software has the quality to manage as well as to control the door access readers. The software is in turn controlled by authorized security personal only.
When you are ensured that you have achieved your desired access control, you can use the software to send all the information to all the IP readers. The reader in turn executes and stores all the commands sent to it by the software. So, even if the network has a glitch and is unable to work, the reader has all the necessary information to keep operating efficiently.
The DB Crystal Matrix Software is included with the door readers for free. The software owns the property to support and control unlimited number of doors and card holders. This is thus a completely featured access control system and provides a precise control for all security problems related to access granting. Real time reporting feature is available that helps you to know who is currently in the secured facility.
EasyWeb Software
When you want to use any web-based framework and want to control access cards on multiple locations then you can include EasyWeb Control software. EasyWeb control software eases the process of distributing the enrollment and management to various people at various locations.
A new inclusion in EasyWeb 2015 software is EasyWeb Mobile. This part of the software helps you to gain control over the software and monitor the system on your cellphone in the cases when you are on the road or any remote area. All you have to do is to download and install the application on your cellphone.

Active Directory Bridge Are there many personal that are controlling your access control system? If yes, it is beneficial for you to select the optional Active Directory Badge (AD-Badge). This software enables you to add users in the system using the Microsoft’s Active Directory. Active Directory Bridge backs the broadcast of particular information and credentials about the people.
IP Door Access Cloud Controle
Keeping in view the advancement in cloud computations, IP door access control platforms are now available in cloud. The services that are provided by the host include installation, administration, and management of ISONAS hardware.
The cloud facilitates you to control and manage unlimited number of doors and access points situated in various areas on your mobile device.

Proximity and Smart Card Door Credentials
You can select the card of your choice from a wide variety of available cards. You can choose thin cards that can simply fit in your wallet or you can choose clamshell card that you can wear on your lanyard or you can choose Key Fobs for your key chain or you can get Cap Tags that can attach to different things.
You can select ISONAS, HID, MiFare, or iClass format or you can select smart card proximity credentials. If you don’t want to use either, then you can select ECKey Bluetooth reader from the options mentioned below.
Example of credentials available:- ISOProx II
- Proxcard II
- DuoProx II
- iCLASS Prox
- Smart DuoProx II
- Proxkey II
- Proximity and MiFare
- DuoProx
- MicroProx
- PhotoProx
- Smart Cards

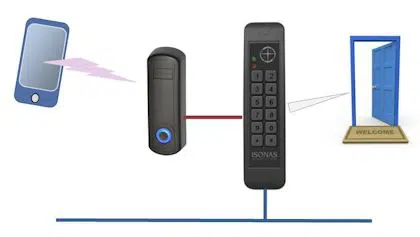
ECKey Bluetooth Reader Uses Your Smartphone as the Credential
When you add the ECKey Bluetooth reader, you can use smart phone to get all services and don’t need to use the credentials. For instance, you can unlock a door, open a gate or even switch on the lights just by using the ECKey module.
In addition, this new device can also be installed in the ISONAS door access control system. Also it can itself be used to create a simple door system. More.
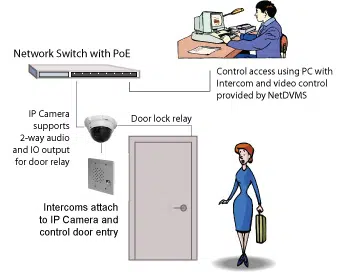
Remote Door Access Control Using an Intercom and IP Camera
If there are such doors in the system that are regularly used by authorized personal but occasionally can also be used by visitors, we recommend you to use our intercoms and IP camera systems for controlling the doors. Entry can also be controlled manually from the PC.
For instance, if a person wants to enter the facility then the intercom will notify you by triggering a beep and the video window will open and you can watch and talk to that person and let him in after assuring yourself.
Various intercom solution are available with us that vary from each other on the basis of application area. More
Resources
Following given are some resources that will provide guidance and help you to understand the technology. If you need any further help then you can contact us for sure and we will guide you in a proper way. Meanwhile, our engineers will make sure that you get the system in accordance with your requirements.
Technical and Application Articles
Comparison of Multimode Door Readers How will you know what door reader you need and which one is best for you? To find the answer to this, please have a look at our buyers guide. The guide provides pros and cons for each type of door reader. In addition, it also includes a comparison of RFID readers, fingerprint, finger vein, facial recognition, and multi-modal readers. The details for those readers is also available that have the capability to detect more than one physiological characteristic.
How to Install an IP Door Control System A review is provided that includes all the necessary information regarding door access control technology and to integrate this technology with IP camera systems.
Door Access Control Review This article comprises of a comparison among older door access technology that makes use of control panels and latest IP door access readers. The article also includes total cost on the implementation of these technologies.
How Network Attached IP Paging and Intercoms can Increase Safety This article is about how Intercoms and IP paging systems helps in enhancing your system’s safety. Everything that you need to know is given in there. For instance, by reading this article you can understand how an intercom can be added that helps you to control a door from a remote area.
Technology Notes Newsletter
If you desire to receive a technical newsletter from us then please just fill out the form.
What does our technical newsletter include? Our Technical Notes newsletter is filled with articles regarding how the technology works and explained examples are provided to make you understand how it is used. It also includes some fabulous technical jokes and fascinating cartoons.
Technical Whitepaper: This technical white paper is all about “How to Create the Complete Safety and Security System”. It explains everything that you need to do to make your world safer and it also includes the information of doing them by integrating IP camera systems, access control and emergency paging systems.
Blogs The blog provided by us is of very useful nature. It describes the principles on the basis of which the technology works. Blog also includes educational notes, methods to accomplish your own calculations and how to decide that which equipment suits you best.
Blogs The videos provided by us gives you an overview of the technology that is being used. You can take a look at our latest video that describes the components of IP camera system and how to set objectives. Following given are the resources that can help you to understand the technology and how it works. If you need further assistance, please contact us for help and we will make sure that your problems regarding your systems are solved.
Technical Support
Understanding a security system can be a tedious task, especially when you are not related to technology. Even when you are related to technology, the technology is evolving so fast that it is harder to catch up. For understanding these systems, you have to know what each component separately is, how each component works and how can it be integrated into the system. PrimeArray is a resource of engineering and integration for all of your projects. Our teams comprises of expert people and we assure you that we can design your system completely. Therefore, don’t hesitate to contact us for assistance.
After you purchase your security system, we will ensure that it works in an exact fashion as desired by you. If you need any assistance regarding the installation of system or integration of various components or technical support of any other kind, please give us a call and we would be happy to help you.
PrimeArray Systems, Inc. 1500 District Ave. Burlington, MA 01803 Tel: 800 433 5133 or 978 455 9488 (outside USA).
